Being a product owner, and new to the technology world is sure bewildering. There is so much to learn in such less time, and everything seems to move at a breakneck pace. Sometimes, it’s hard to catch on.
There are so many technical terms that we use in our daily life, but don’t understand.
For example, we often tell our friends that “I can’t come online, my server is down,” or ‘I saw this amazing restaurant on the net,’ but if I ask you, what is the Internet? Or what is a server? You might get confused or just search it on the “web.”
See, even to know about one technical thing, You still have to search it on the other.
It’s all connected.
It’s even more vital for you if you are planning on launching a product. Also though it has nothing to do with the web, you still have to know about it.
Let’s say; You hire a team, how would you know they are doing the right thing? Or if they are taking the right steps?
So, It’s important to know the basics at least. There is no running away from this. The sooner you learn, the better it will be for your product and company.
Let’s start from the basics:
What is the Internet?
The definition you will find anywhere will tell you, “it is a network of networks which users from any computer can access, with permission.”
True, but this is not enough if we want our product to take on in the market. We must know more.
So, what we know is that the Internet is a vast interconnection of networks composed of millions of devices.
What we don’t know is precisely how this Internet reaches our computers?
Through waters, not literally, though.
You will be surprised to know that fiber optics transmits 99 % of the data you access through your devices from under the ocean. These wires are also called submarine communication cables.
There are millions of very long wires under the sea; these wires are buried almost 29,000 feet deep.
There could be sharks trying to eat your data.
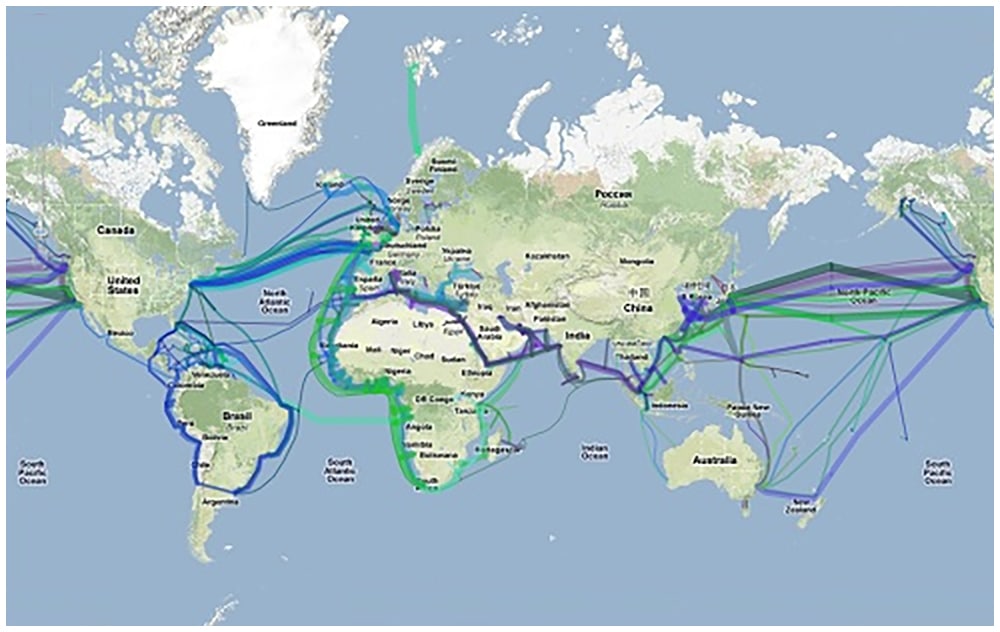
The fiber optic wires are installed by tier one companies like Google, and these companies sell it further to level 2 companies, who sell it also to the layer three companies. i.e., your local broadband.
Some other basic terminologies that are crucial for a product owner to be aware of, before he launches the product in the market, are:
Hosting Servers:
Here’s how to detect your website on the web.

A web hosting server is like a supercomputer, that allows an individual or company to make their website detectable on the worldwide web.
It assigns virtual memory to other companies.
Every device we use comes with a unique MAC address; this is the physical address of the device through which you can identify it on the computer networks, it is directly assigned to the hardware of the device.
Whereas, an IP address, an acronym of Internet Protocol, is a unique number that is linked to all the online activity that you do. The IP address attaches an “electronic-return address” for all the things that you do on the web, and this address is the IP address to your connection.
Your IP address changes as soon as you turn your connection or device.
However, it can still be used for identifying your device. It is mostly assigned by the hosting server automatically, with the allocated virtual memory.
An IP address may look like this:
2402:3a80:9d5:d4c1:d5c1:20da:11f8:ea3a
Or
192.168.1.66
Although searching the exact IP address may take you to the website you want to go to, however, it is very complex to remember or even search for something like this.
So to sort that problem, Stanford Research Institute came up with a file text name that mapped the hostnames to the IP addresses.
In simpler words, the domain name server masks the IP address, for you to avoid the hassle.
Now you can just search by the domain name, and you would land on that particular website.
Technology has sure made our lives easier.
URL:
The website address.
When we copy a link, we often see the option that says ‘copy URL’, it is that common, yet we know very little about it.
A URL- Uniform Resource Locators are the addresses provided by the web browser to the internet pages. A URL allows you to bookmark or locate the page or file of your choice. You might also call them links.
Searching for a particular link will take you directly to your desired page location.
A URL might look like this: https://www.hestabit.com/
URL is made up of three parts:
Protocol: while there are other protocols too, the most popular one used majorly by web pages is HTTP or HTTPS. It is the part of the URL ending with .com//
Host: Also known as the Top-Level domain, is a part of the domain that comes after the dot. For example: .in, .com, .net, .edu, and so on.
File Name: It is the page name itself.
The Internet is undoubtedly essential since the world is getting digital, but how do you use it? What are its technicalities? Remain a question laymen could never answer.
Not anymore, though.
The Internet works on a set of defined rules, often known as protocols. I have explained some of them below:
HTTP and HTTPS:
Gateway for communicating to your websites.

HTTP stands for Hypertext Transfer Protocol. If you type HTTP:// in the address bar before the domain, it would tell the browser to connect over to HTTP. It sends and receives data on the Internet. It is a protocol used for you to communicate easily with other websites.
The browser sends a request to the server through HTTP, it then comes back with a response. This response message contains completion status.
When your webpage has this prefix, the links and texts and pictures should work fine on your page.
HTTPS stands for Hypertext Transfer Protocol Secure. If you see HTTPS before the domain, know that the webpage is secured by adding a particular layer of encryption just to secure your data. This layer of security hides your personal information and passwords from other users.
Online bank accounts or e-commerce sites that require you to share your credit card details or some other personal information mostly uses this.
Make sure to notice it before you put in all your personal information.
The SSL protocol is widely used to make your data secured; it provides a channel between two machines operating on the web. It is a secure channel. This is used when there is a need for securely connecting the webserver to the web browser.
Although the Internet works on structured rules, there are other components of it too, that makes it a wholesome platform to grow your business.
Some other rather essential components of the Internet are:
Encryption and authentication:
Security is a priority.

Encryption is a technique that lets only the authorized party access the data. Encryption jumbles up the data, mathematically, to protect it from hackers. It turns personal data into jargon that only trusted users can interpret.
Encrypting your web page makes your users trust you. A user will not think twice before entering their personal information if they are aware that your site is encrypted.
When encryption is reliable, all the personal information that one feeds is kept private.
Authentication is the process through which the website knows that you are the person you are claiming to be. For example: when you log in to your details that match the website database, it will know that you are the right person.
Cloud Computing:
Rent out your webspace.

Cloud computing is an easy and cost-efficient computing service.
It is a term used to describe the process of renting out a data center.
This is used by most business owners, rather than buying their own computing services, companies simply rent access to anything, be it storage or an application from a cloud service provider.
The information that you wish to store and access anytime is accumulated in the cloud.
For example, you upload your pictures on google drive when you are at your home, those same pictures will still be accessible even when you travel thousands of kilometers. That is the vast space cloud computing provides you with.
By the owner’s perspective, it goes easy in their pocket too.
It saves them the cost and complexity of owning and maintaining their own IT structure; instead of that, whenever they need something, they can simply pay and use it, that too pay just for what they want, no extra expenditure.
Other than this, cloud computing also stores files all in one space and allows access through more than one device, so many users can collaborate on the same record at the same time. So, with being cost-efficient, it is time-efficient too.
Cloud services are provided by many companies like; IBM, Microsoft, Cloudera, Amazon Web services, Google Cloud, ThousandEyes, and many more.
Firewall:
Create a protective wall.
A firewall is a security device that protects your network from malicious traffic like hackers and viruses.
It closely monitors incoming as well as outgoing traffic and allows or blocks the data users according to the set security rules. The firewall provides an additional layer of security by becoming a barrier against unwanted sources.
It is a known fact that whatever is up on the Internet is accessible to almost everyone, if you wish to restrict your data to only selected users, you can use the firewall to do so. The software allows you to even publish your data to a specific location, targeting a particular set of audience.
Imagine, building up a website investing both money and time and ultimately succumbing to hackers or viruses. No owner would want that fate. The firewall acts as your guardian in such times. If you enable this while you upload a file through SSH or HTTP, it will only be accessible by the devices you have permitted.
A Firewall is the best software to protect your data from any kind of malware.
Malware:
The Intruder of your space.

Malware is referred to any ill-natured software designed by hackers, mainly with the aim of:
- Stealing your personal information
- Taking control of your computer.
- Manipulate your device to seek money or purchase something.
To avoid being bait to the hacker’s malice, it is better to use the Operating System “Linux”
Linux is an open-source operating system that manages both the hardware and software of the system, the OS bridges the software and the physical resources on which you work.
Linux is comparatively safer and more secure than much other software out there. The only limitation to the software is that you abide by its rules, as long as you follow the rules, you are on track, else it can backfire.
HTML, XML, AND JS:
Everything that you see on your webpage.

Hypertext Markup Language is a programming language used by web pages. HTML is everything that you see on your webpage. It is all the documents that are designed to be on your webpage. It enables the users to create headings, links, paragraphs, and also structure them in their web pages and applications.
For example, you can add a paragraph in HTML by placing it between “<p>”
<p>add this para here!<p>.
This step enables you to add text to your webpage.
XML stands for Extensible Markup Language, XML is designed to describe the documents that you wish to display on your web page. It stores your data and transports it according to your needs.
Put simply; It is used to classify and database the content of your webpage.
JAVASCRIPT
Javascript is a programming language that lets you use complex features, easily on your website. What earlier needed maybe five steps to form, now need only two, thanks to javascript.
When you open a site that has all- animations, interactive maps, content updates, graphics, know that Javascript has been appropriately implemented. JS is the basics of every single code written on the web; this script allows the client side to interact with the users. It holds object-oriented capabilities.
Many applications that are known worldwide are built using JavaScript out of them some of the most widely recognised applications are Yahoo, LinkedIn, Paypal, Netflix, Uber, GoDaddy and Ebay.
For example, there are many pages on the web that don’t allow you to copy their content; they set those rules through javascript. A person well-read in the field can disable the feature and copy the content, as he likes. Although, as soon as the page reloads, it will show an error, but the settings can be changed for a moment.
To be able to do this, and to stop someone else from doing this on your web page, it is essential to be well aware of javascript.
All these components collectively make up the Internet. If you know what they are and how they work, you will be able to conquer the Net.
Now, you know what you should know. Don’t waste any more time, get in touch with our tech team, and build up your dream product.
You are all set to go!