“It takes 20 years to build a company’s reputation and 20 seconds of a Cyber incident to ruin it.”
When you dream of building your company as an aspiring entrepreneur, all you want is to get off the starting line. You may think that the right idea is the key to business success. However, I differ from this thought process. For me, it is always about execution and consistency. One needs to continuously keep about everything in the frame, right from the finances to marketing to security and especially security when it comes to small enterprises. People never think it may happen to them.

If I go by the recent Harvard research study by Business Analytic Services survey. It says that more than half of the small business owners remain locked into this magical line of thinking that data cybersecurity can only be a threat to multinational companies. Many of us in the web development industry are blissfully unaware of the danger that cybercrime possesses to the health of our organization.
I hate to burst the bubble, but the incidents of hacking in small companies may not make up to the news. Still, small businesses are being targeted and destroyed by the cybercriminals at an astounding rate. We often hear terms such as data breaching, trespassing, big data breaking and the most common one cyber attack when we talk about data leak incidents in the industry. However, all of them are very distinctive, and as a business owner, you are obligated to be aware of your security terms. I think it’s time we start taking this seriously and understand the danger around our workplaces.
Therefore, to guide you towards economical security solutions, I have assorted certain precautions and security measures that you can employ to your systems to create a safe and secure environment for your data. But before we hop on to that, we must understand the concept of Cyberattack and hacking.
In this article, we will talk about
- What is a Cyberattack?
- What are some major Cyber attack trends?
- How are small companies shut down within six months?
- Reasons why your business can be the next target?
- How to secure your digital assets?
- Cyber security tools you need
What is a Cyberattack?
A cyber attack is basically an assault that is launched by the cybercriminals using multiple systems or networks. A cyber attack can maliciously steal data, disable computers, or even use a breached system as a launch point for other attacks. There are various methods to launch a cyber-attack such as a denial of service, phishing, malware and ransomware, among other techniques.
The world is now facing a 5th generation cyber attack. Gone are the days when it was just about stealing and selling. Your data now reaches the market that runs without a name and location.
Let’s talk about some of the most significant and major cyber trends in our industry.
The Sunburst Attacks
The researchers named it sunburst, and it is said to be the most severe and sophisticated attack ever seen or heard. The attack left a profound impact on major US and UK government offices and private sector organizations.
The series of this attack was made possible when hackers embedded a backdoor into SolarWinds software updates. Over 18,000 government offices and companies downloaded this software that seemed like a regular system update. The hackers extracted all the assets of these companies and gave the public access to the data.
Ransomware attacks
State government and small vendors are the biggest victims of this attack. In a 2020 software study, a 50% increase is noted in the ransomware attacks with healthcare as the most intended target industry. The top ransomware attacks among all are Ryuk and Maze.
Software supply chain attacks
This is a destructive attack under which the hacker installs a malicious code in the legitimate software by infecting and changing one of the major blocks on which the entire system relies. When it comes to supply chains, they are only as strong as their weakest chain link. Not long ago, In the Shadow Hammer attack, hackers implanted a code in the ASUS Live update utility that helped them install backdoors on millions of remote computers.
Evasive phishing cyber attacks
Phishing is the most popular technique and continues to be the biggest threat in the cybersecurity line. Last year, a surge was noted in business scams and business email compromise (BEC) where victims were threatened through blackmail or impersonation into making a payment.
Generally, evasive email scams include images of the text embedded in the body or encoded emails that mix with HTML character entities.
Cloud attacks
We are the generation that doesn’t like storing anything on our local storage. The growing trend of public cloud environments has led to an increase in cyber attacks targeting sensitive data and resources residing in these platforms. From the past two years, misconfiguration is one of the leading causes of aggression and data theft incidents.
Mobile device attacks
The spiteful hackers are now adopting new methods and techniques from the general threat landscape to the mobile world. In correlation to the growing use of banking and eCommerce mobile apps, the actors are now able to steal credentials, payment data and funds from the victim’s bank account.
Apart from these trends, identity theft is also reaching new heights. Hackers exploit one information to break into other accounts and then attempt to steal identities.
Now, you must be wondering if all these attacks are probably a danger to a well-established organization that contains more valuable assets. Well, that’s partially true. They do have valuable and sensitive assets that can be worth billions, but as big as the organizations get, they have a substantial budget to hire an entire department to secure their data systems. Small and medium scale enterprises often stick to this assumption and not pay attention to these threats. That’s what results in a cyber activity in your business.
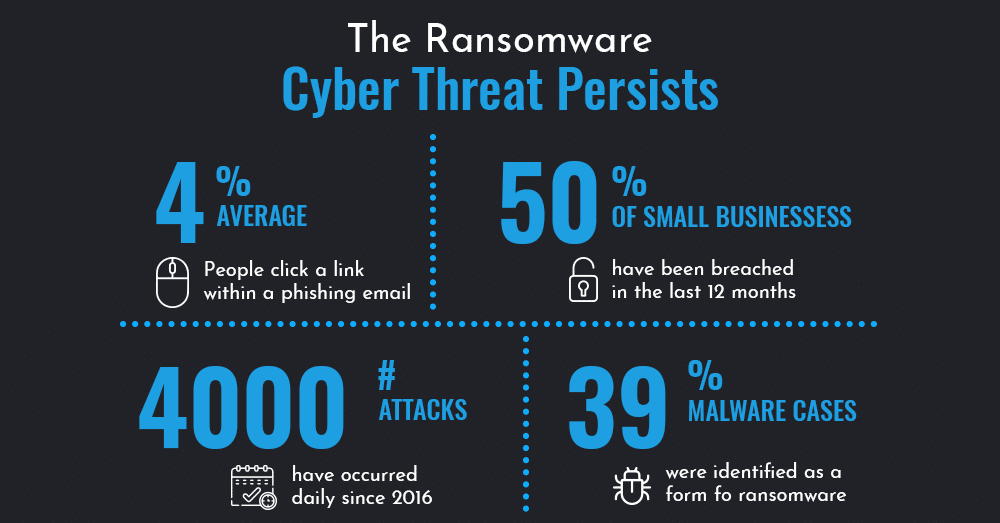
Companies Shut Their Doors Within Six Months
National Cyber Security Alliance (NCSA) reports that approximately 60% of the companies that succumb to the cyber-attacks and data breach incidents, turn themselves down within six months. The study also concluded that instead of zeroing it on high profile businesses, hackers actually prefer to swoop in on the little ones with explicitly targeting business data. After a cyber incident, such companies usually run out of business due to lack of projects and clients and eventually close their doors.
Reasons Your Small Business Can be the Next Target
I believe the very next thought that strikes your head would probably be you have got anti-virus software and a firewall and trustworthy employees for your small company. Besides, you haven’t been a target yet. But there is that word “yet”. So you know there are chances of you being the next. Let us see why
Your business is more exposed
While multinational corporations have significant funds and personnel available to employ strict protocols and security, small ones probably don’t. Instead, they tend to rely on their staff’s limited knowledge. It’s reported that this is the primary cause of why small businesses do not take security issues seriously.
Your business has valuable and sensitive data
Believe it or not, but it doesn’t take much to catch the attention of a hacker. They understand the real value of a small business data and even a few records and credentials are enough for them to earn millions.
How, you ask?
A typical small business has employee records that hold personal information and health records of the clients in high demand and financial records such as credit card numbers. Hackers extract full information and sell them in the black market. This is a lucrative source of revenue for cybercriminals.
Your business is more vulnerable to phishing attacks
Small businesses are often the target in the hit list of spear-phishing tactics that occur when a hacker attempts to steal credentials by posing as a highly authorized person. Their most common approach is to take on the identity of the organization’s IT technician in order to gain credentials to internal network access. This makes the entire activity untraceable and is ultimately safer than other hacking techniques.
Despite the prevalence of Cyberattacks, the point is 99% of small and medium scale companies are not effectively protected. If you hate for someone else to get their hands on your data, start taking measures and protecting your valuable digital assets not only from the hackers but also from every other person that can be a threat to your business.
How to Protect your Digital Assets
Looking at how advanced the attacks have turned, the security solutions should also be equivalent to them. However, many business owners may not realize all of the digital assets the company owns. Let us take a quick glance at what comes under the digital asset category.
Your Digital assets may include
- All your social media accounts and posts.
- Companies’ website and its entire content and domain
- Employee list and information
- Customer and client information
- Business processes such as manuals and spreadsheets
- Photos and visuals that belong to the company
- Apps that you have developed under mobile application development
- Intellectual belongings like patents and trademarks.
Now, here are a few tricks on how you can protect your business data and assets.
Secure the WiFi and stay Updated
The most common way for a hacker to get hold of your data is by gaining access via security loopholes. Therefore, ensure that you have updated your operating systems, including cloud-based applications that have your data stored.
Other than that, WiFi is a key component of every business these days. Hence, you must follow the best WiFi security tips in the market to maintain safety. Besides, enable the firewall and regularly update the software and the firmware. Change your network name from time to time. Most WiFi also provide the facility of encrypting the data; in that case, take advantage of the feature.
Keep access limited.
Not everyone in your company requires access to your digital assets. So, keep access limited to the team members who use them often. Under your authority, you can set permission in certain applications and can choose who can edit, see or download your assets.
If you have a remote business, be sure to have a password protection tool that secures your credentials online in an encrypted format.
Employee education is also a big part of protecting your company’s valuable data. Most of the data breaches occur due to the accidental loss of a document or device by an employee. So try educating your employee with cybersecurity practices.
Secure Authentication:
To add an extra sheet of security, you can also enable secure authentication such as two-factor authentication (2FA). In such a process, after you enter the process, you would require to enter a second one-time password or answer a question that is usually sent on your phone via text message to confirm the user identity.
Cyber Insurance
Another thing that can save your company from a cyber attack is investing in cyber insurance. This can protect your business against all the internet-based risk. Moreover, If somehow the hackers still reach your assets, cyber insurance can cover the cost of notifying customers, lawsuits, crisis management, and investigation processes.
The Cyber War Is On: Final Thoughts

Besides, all the precautions that are mentioned above, you can also rely on security tools. Here are one of the most popular security tools of 2021 that you can get your hands on:
- PKI Penetration
- CIS
- WireShark
- LifeLock
- Malwarebytes
- Webroot
- Intruder
- BitDefender total security
There is an estimation of Cybercrime cost placed somewhere between 500 million to trillion dollars in the market. The real threat is the fact that this cyberwar is not going to stop. However, as a socially responsible enterprise, we must educate every business with the most economical and reasonable solutions to all the problems. Let us make this world a safer place to live.